HACKING ZONE
Wednesday, 4 July 2012
Saturday, 30 June 2012
Hack Gmail,Myspace,Facebook accounts Using Rinlogger
Keylogging is one of the Easiest ways that you can use to Hack Gmail, My space,Face book accounts .If your new to the concept of key logging I would suggest you read my previous article What are key logger before reading this one
Hack Gmail /Myspace /Facebook accounts Using Rinlogger
Concept :-
For Rinlogger(keylogger) to work, the victim has to install a server file on his computer. This server file keeps on recording and sending all typed keystrokes from victim computer. No doubt, these keystrokes contain the victim’s Gmail password. All such keystrokes are sent by server in your mailbox and thus, you can easily hack Gmail account of your friends using this method.
Working :-
1. First a fall download Rinlogger from Here & to get the password Click Here
3. Now enter the following information
Email - your email address (gmail recommented)
Account password - Your email password
Keylogger Recipients - Enter your email address
finally click next as shown
5. Now change Install keylogger to “Enabled”. Name the file anything you want and select Installation path as “Startup”,Finally click next
6. Now change enable downloader to “Enabled” & check once only (requires install) ,finally click next 3 three times
7. Now change enable file binder to “Enabled” , and select any application or file document to bind by clicking File binder setup as shown , Then click next and change Steal passwords to "enabled ",finally click next two times
voilà ,You have successfully created a keylogger server file. Now, simply send this file to your victim via email , Once the victim runs our keylogger, we will get key logs every 5min via email as shown
Note :-
AV scan result shows this key logger is currently 100% FUD , but since its a free /public key logger it will be detected by anti viruses very soon .So my advice is use this key logger as long as it is FUD and make the most out of it .We also recommend you to use –winspy keylogger or Sniperspy which are FUD for life time (Fully Undetectable).
Tuesday, 26 June 2012
Spy Bot for Nimbuzz
Hi there Nimbuzzers, it's been a quite while i'm posting here. One of our Nimbuzzer has made a cool Bot for us. Introducing the "Spy Bot", a bot that can steal Nimbuzz avatars, personal messages and more.

if you like to grab the avatar image of some one eles, you might need a avatar grabber software or type the url on your browser,but if you are a mobile user,Spy Bot will help you to steal the others avatar with just few commands.check some more features of the bot.
BOT FEATURES
Retrieve the display name(Nick Name) of any nimbuzz user.
Retrieve the personal message of any nimbuzz user.
Retrieve the link to see avatar image of any nimbuzz user
Retrieve the list of users in a chatroom without entering.
How to Setup the Bot
Note that,this bot is not available in the N-World,where you add Bots to your list.all you have to do is add the bot id manually using your nimbuzz.add the following ID to get the bot
..spybot..@nimbuzz.com
once you add the bot,it will be online in your list. start a chat session with the bot and type "Commands",so you will get the instructions,how to use the bot.i have demonstrated the commands in use by the images below.
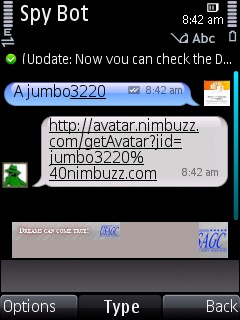
Retrieving Avatar link
type a<space>Nimbuzz ID you want
example : a jumbo3220(it doesn't matter, whether ''a'' is capital or simple letter and you dont need to type @nimbuzz.com at the end of the ID)
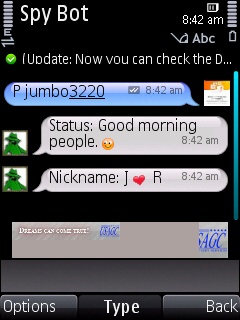
Retrieving Display Name and Personal Message
type p<space>Nimbuzz ID
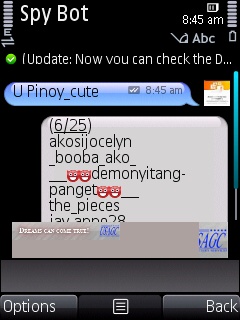
Retrieving a List of Users in a Chat Room
type u<space>Chat Room Name
example : u pinoy_cute (No need to type @conference.nimbuzz.com at the end)
Cool right? no need of xml scripts anymore to see the users in a chat room.well if you find any issue with the bot ,simply contact amit986@nimbuzz.com
Monday, 25 June 2012
East Way To Crack fake Id
step 1: 1st of all you make a room.
step 2: Put a ban bot mafia bot here or chatting warrior bot here
step 3: not take fake symbols
ऽ ा ि ॊ ो ौ ् ी ु ू ृ ॄ ॅ ॆ े ै ॉ ॐ ॑ ॒ ॓ ॔ ॠ ॡ ॢ ॣ । ॥ ॰ ¡ ¿ ¦ † ‡ ← → ↑ ↓ ↖ ↗ ↘ ↙ ↔ ⇐ ⇑ ⇒ ⇓ ⇔ … · • ¶ ½ ⅓ ⅔¼ ¾ ⅛ ⅜ ⅝ ⅞ ฿ ¢ $ € ₭ £ ₦ ¥ ₩₪ ✓ ✗ ♀ ♂ ± −− × ÷ ⋅ √ ≠ ≤ ≥ ≡ ∼ ≈ ∞ ∅ § © ® ™ Á á Ć ć É é Í í Ó ó Ś ś Ú ú Ý ý Ǿ ǿ À à È è Ì ìì Ò ò ò Ù ù  â Ĉ ĉ ĉ Ê ê Ĝ ĝ Ĥ Ĥ ĥ Î î Ĵ ĵ Ô ô ŝ Ŝ Û û Ä ä Ë ë Ï ï Ö ö Ü ü ÿ à ã Ñ ñ Õ õ Å Å å Ç çç Č č Š š ŭ Ł ł Ő ő Ű ű Ø ø Ā ā Ēē Ī ī Ō ō Ū ū ß Æ æ Œ œ Ð ð Þ þ| Ά Γ Δ Έ Ή Θ Ι Ί Λ Ξ Ό Π Σ Ύ Φ Ψ Ω Ψ Ώ α ά β γ δ ε έ ζ η ή θ ι ίκ λ μ ν ξ ο ό π ρ σ ς τ υ ύ φ χ ψω ώ ±½¼¾©®ª°º¹²³₪´¯`¦ζλαČΦΨΩ«»єΞ¶ ■●○▲Δ▪▫İ•¿™¥¢¤¬◊∑≤≥⅞₪∩† ₫ ‰‹ ›‼‾ⁿ₣ ₤℅ℓ℮⅛⅜⅝⅞←↑→↓↔↕↨∂∆∑− ∕∙√∞∟∩∫≈≠≡≥⌂⌐⌠⌡─│┐└┘┘ ├┤┬┴┼═║╒╓╔╕╖╗╘╚╛╛ ╝╞╟╠╡╢╣╤╥╦╦╨╩╪╫▐░ ▒▓■□▬►▼◄◊◘◙◦☼♀♂ ♠♣♥♦♪♫―‘’ ‘ ’ “ ”„ ‚°×π‰≈– —‡☺☹ Russian : Аа Ии Сс Ъъ Бб Йй Тт Ыы Вв Кк Уу Ьь Гг Лл Фф Ээ Дд дэ Мм эм Хх Юю Ее Нн Цц Яя Ёё Оо Чч Жж Пп Шш Зз Рр Щщ ;̣̉;̣̉̃́̀ ]̲̲̅̅ H̲̲̅̅3̲̲̅̅H̲̲̅̅H̲̅§҉¨¨¨¨¨¨ˉ҆҅o̲̲̲̿̅̿®© м̲̅Д̳̿Χ҉♥♣●ऋळखऔईछऊईळ ΞФ๛€ईӁ ∫Ξ∫ωईछ°° ฆỜỜๅ ש๏φ๑ॐʒ«Ӂ̶̲̅Ʒऊई _‗ـ −ΞΞـ‗_‗__‗҉ـ−ˉ‾‾ˉ−ــ ™♥-ــ-ـ-ـ ळखऔॐ»ฆ¥̲̅ळ₪¶̳̳̿͋͌͊̿ 3͠b͠o͠͠o͠d͠ʒ͡Ξ҈−҉ ôΞô♪♪♪๛ ש ωƷʒ̶̶Ʒ M̶S̶A̶E̶E̶R̶м²<͡ô ˛¸¸˛.̶.̶.̶.̶җ ¨.¸¸.¨°™██ ζζ∫∫∫∫♂♂ ﮧֻﮧֻﮧֻﮧֻﮧֻﮧ ำำใใใใ๗๗ ◊◊≈҉≈≈҉≈‗‗‗‗‗‗‗‗¦∕ˉ¦∕ˉ ฆฆ░░∫∫|ୃୃୃ|ୃୃୃ|ୃୃୃıı̉†‡†‡ΩΩ ↑→↓↔↕↨∂∆├┤├┤◘ ◙◦♥☺☼☼♀♂♠♣♥♦♪♫~ ∞~∞♫♫¶¶ ╛ ══╩ª┼┴÷ ± ¸ µ ÷ þ †½ ¼ ¾ ﻻﺇﻟﻪ ﺇﻻﺍﻟﻠﻪ ﻣﺤﻤﺪﺭﺳﻮﻝ ﺍﻟﻠﻪ¤ﺃﺷﻬﺪﺃﻻﺇﻟﻪ ﺇﻻﺍﻟﻠﻪ ،ﻭﺃﺷﻬﺪﺃﻥ ﻣﺤﻤﺪﺭﺳﻮﺍﻟﻠﻪﺻﻠﻰ ﺍﻟﻠﻪ ﻋﻠﻴﻪ ﻭﺳﻠﻢ .arabic letters ﺍ ﺏ ﺕ ﺙ ﺝ ﺡ ﺥ ﺩ ﺫ ﺭ ﺯ ﺱ ﺵ ﺹ ﻁﻅ ﻉ ﻍ ﻑ ﻕ ﻙ ﻝ ﻡ ﻥ ﻩ ﺃ ﻱ хъжэбюзщшгнекуцйфы?Ш»«₪ΔΛΞΩΨ¦¶ø↑↓? ↲◊®©™½¼¾÷×¹²³°ºªώ±• ۰¿@ £þ€$$¥¤ώλ βανψφðΘιŁŊ¡И׃ֶׁ ַאבג σ דהוזחטיךכלםמןנя סעףפץצקרשתװױײ׳״ ،؛؟ ﺀﺁﺃﺃﺅﺇﺋﺎﺑﺔﺗﺠﺤﺨﺪﺫﺭﺯﺳﺸﺼﻂ ﻇﻌﻐـﻒ ﻗﻜﻠﻤﻨﻬﻮﻯﻲًٌٍَُِّْٓٔ ٠١٢٣٤٥٦٧٨٩ ؟ðя Ł ٤٢؟ ₧Ŧ←→↑↓↖↘『|̲̅|̲̅|̲̅ ①②③④⑤⑥⑦⑧⑨⑨⑩父VⅣ ΦΧΨΩΪΫάέήίΰαβγδεζηθι κλμνξοπρςστυφχψωϊϋόύώЁЂ ЃЄЅІЇЈЉЊЋЌ ЎЏАБВГДЕЖЗИЙКЛМНОПРТУФ
step 5 : now make id and ban it by ban bot if id get banded it mean it is on nimbuzz server try the different combination n ban.
step 6 : now open cracker n start cracking ban ids lol download from cracker here.
enjoyyyyyyyyyyyyyyyy the trick ;)
step 2: Put a ban bot mafia bot here or chatting warrior bot here
step 3: not take fake symbols
ऽ ा ि ॊ ो ौ ् ी ु ू ृ ॄ ॅ ॆ े ै ॉ ॐ ॑ ॒ ॓ ॔ ॠ ॡ ॢ ॣ । ॥ ॰ ¡ ¿ ¦ † ‡ ← → ↑ ↓ ↖ ↗ ↘ ↙ ↔ ⇐ ⇑ ⇒ ⇓ ⇔ … · • ¶ ½ ⅓ ⅔¼ ¾ ⅛ ⅜ ⅝ ⅞ ฿ ¢ $ € ₭ £ ₦ ¥ ₩₪ ✓ ✗ ♀ ♂ ± −− × ÷ ⋅ √ ≠ ≤ ≥ ≡ ∼ ≈ ∞ ∅ § © ® ™ Á á Ć ć É é Í í Ó ó Ś ś Ú ú Ý ý Ǿ ǿ À à È è Ì ìì Ò ò ò Ù ù  â Ĉ ĉ ĉ Ê ê Ĝ ĝ Ĥ Ĥ ĥ Î î Ĵ ĵ Ô ô ŝ Ŝ Û û Ä ä Ë ë Ï ï Ö ö Ü ü ÿ à ã Ñ ñ Õ õ Å Å å Ç çç Č č Š š ŭ Ł ł Ő ő Ű ű Ø ø Ā ā Ēē Ī ī Ō ō Ū ū ß Æ æ Œ œ Ð ð Þ þ| Ά Γ Δ Έ Ή Θ Ι Ί Λ Ξ Ό Π Σ Ύ Φ Ψ Ω Ψ Ώ α ά β γ δ ε έ ζ η ή θ ι ίκ λ μ ν ξ ο ό π ρ σ ς τ υ ύ φ χ ψω ώ ±½¼¾©®ª°º¹²³₪´¯`¦ζλαČΦΨΩ«»єΞ¶ ■●○▲Δ▪▫İ•¿™¥¢¤¬◊∑≤≥⅞₪∩† ₫ ‰‹ ›‼‾ⁿ₣ ₤℅ℓ℮⅛⅜⅝⅞←↑→↓↔↕↨∂∆∑− ∕∙√∞∟∩∫≈≠≡≥⌂⌐⌠⌡─│┐└┘┘ ├┤┬┴┼═║╒╓╔╕╖╗╘╚╛╛ ╝╞╟╠╡╢╣╤╥╦╦╨╩╪╫▐░ ▒▓■□▬►▼◄◊◘◙◦☼♀♂ ♠♣♥♦♪♫―‘’ ‘ ’ “ ”„ ‚°×π‰≈– —‡☺☹ Russian : Аа Ии Сс Ъъ Бб Йй Тт Ыы Вв Кк Уу Ьь Гг Лл Фф Ээ Дд дэ Мм эм Хх Юю Ее Нн Цц Яя Ёё Оо Чч Жж Пп Шш Зз Рр Щщ ;̣̉;̣̉̃́̀ ]̲̲̅̅ H̲̲̅̅3̲̲̅̅H̲̲̅̅H̲̅§҉¨¨¨¨¨¨ˉ҆҅o̲̲̲̿̅̿®© м̲̅Д̳̿Χ҉♥♣●ऋळखऔईछऊईळ ΞФ๛€ईӁ ∫Ξ∫ωईछ°° ฆỜỜๅ ש๏φ๑ॐʒ«Ӂ̶̲̅Ʒऊई _‗ـ −ΞΞـ‗_‗__‗҉ـ−ˉ‾‾ˉ−ــ ™♥-ــ-ـ-ـ ळखऔॐ»ฆ¥̲̅ळ₪¶̳̳̿͋͌͊̿ 3͠b͠o͠͠o͠d͠ʒ͡Ξ҈−҉ ôΞô♪♪♪๛ ש ωƷʒ̶̶Ʒ M̶S̶A̶E̶E̶R̶м²<͡ô ˛¸¸˛.̶.̶.̶.̶җ ¨.¸¸.¨°™██ ζζ∫∫∫∫♂♂ ﮧֻﮧֻﮧֻﮧֻﮧֻﮧ ำำใใใใ๗๗ ◊◊≈҉≈≈҉≈‗‗‗‗‗‗‗‗¦∕ˉ¦∕ˉ ฆฆ░░∫∫|ୃୃୃ|ୃୃୃ|ୃୃୃıı̉†‡†‡ΩΩ ↑→↓↔↕↨∂∆├┤├┤◘ ◙◦♥☺☼☼♀♂♠♣♥♦♪♫~ ∞~∞♫♫¶¶ ╛ ══╩ª┼┴÷ ± ¸ µ ÷ þ †½ ¼ ¾ ﻻﺇﻟﻪ ﺇﻻﺍﻟﻠﻪ ﻣﺤﻤﺪﺭﺳﻮﻝ ﺍﻟﻠﻪ¤ﺃﺷﻬﺪﺃﻻﺇﻟﻪ ﺇﻻﺍﻟﻠﻪ ،ﻭﺃﺷﻬﺪﺃﻥ ﻣﺤﻤﺪﺭﺳﻮﺍﻟﻠﻪﺻﻠﻰ ﺍﻟﻠﻪ ﻋﻠﻴﻪ ﻭﺳﻠﻢ .arabic letters ﺍ ﺏ ﺕ ﺙ ﺝ ﺡ ﺥ ﺩ ﺫ ﺭ ﺯ ﺱ ﺵ ﺹ ﻁﻅ ﻉ ﻍ ﻑ ﻕ ﻙ ﻝ ﻡ ﻥ ﻩ ﺃ ﻱ хъжэбюзщшгнекуцйфы?Ш»«₪ΔΛΞΩΨ¦¶ø↑↓? ↲◊®©™½¼¾÷×¹²³°ºªώ±• ۰¿@ £þ€$$¥¤ώλ βανψφðΘιŁŊ¡И׃ֶׁ ַאבג σ דהוזחטיךכלםמןנя סעףפץצקרשתװױײ׳״ ،؛؟ ﺀﺁﺃﺃﺅﺇﺋﺎﺑﺔﺗﺠﺤﺨﺪﺫﺭﺯﺳﺸﺼﻂ ﻇﻌﻐـﻒ ﻗﻜﻠﻤﻨﻬﻮﻯﻲًٌٍَُِّْٓٔ ٠١٢٣٤٥٦٧٨٩ ؟ðя Ł ٤٢؟ ₧Ŧ←→↑↓↖↘『|̲̅|̲̅|̲̅ ①②③④⑤⑥⑦⑧⑨⑨⑩父VⅣ ΦΧΨΩΪΫάέήίΰαβγδεζηθι κλμνξοπρςστυφχψωϊϋόύώЁЂ ЃЄЅІЇЈЉЊЋЌ ЎЏАБВГДЕЖЗИЙКЛМНОПРТУФ
step 5 : now make id and ban it by ban bot if id get banded it mean it is on nimbuzz server try the different combination n ban.
step 6 : now open cracker n start cracking ban ids lol download from cracker here.
enjoyyyyyyyyyyyyyyyy the trick ;)
Saturday, 23 June 2012
FUD Crypter Free Download - Bypass Antivirus Detection
What Is Crypter?
Crypter is a software used to hide our viruses, keyloggers or tools from antiviruses so that they are not detected by anti viruses. Thus, a crypter is a program that allow users to crypt the source code of their program to Bypass antivirus detection
What Does UD And FUD Mean?
UD means undetected, so only a few antivirus programs detect it. FUD means fully undetected, so no antivirus detects it
FUD Crypter Free Download - Bypass Antivirus Detection
1. Download Free FUD Crypter from Here & Download the Password From Here
2. Open the FUD Crypter select server file as your Keylogger file or RAT file , Then go to Appearance tab check custom icon and select your icon ( i have included a icon pack also )
3. Finally click " Crypt " , Now you will get a Crypted file which is totaly undetectable by antiviruses.
AV Scan Results :-
As an example I used this crypter to crypt my ardamax keylogger and found out that this crypter is 100 % FUD
Ardamax keylogger Before crypting
Ardamax keylogger After crypting
Note: This a public crypter and Hence it will remain FUD for only few weeks , So use this crypter at the earliest.we also recommend you to use winspy keylogger or sniper keylogger Which are FUD for life time
What are KeyLoggers ?
A keylogger sometimes called a spying software is a small program which is used to monitor a local or a Remote PC, Keyloggers now a days are so easy to use that a person with even a basic knowledge of computers can use keylogger.Once a keylogger is installed in your computer it can monitor each and every keystroke typed on your computer, thus key logger can be used for many purposes such as monitoring your children , employees and many more
There are Two main types of keyloggers that you should be aware of
Hardware Keyloggers
This type of keylogger is a piece of equipment that is physically attached to ones computer, typically between the keyboard and the machine itself. While this type is the most powerful and readily available (try a Google search for ‘keylogger’ and you’ll be shocked), it also requires direct access to a machine to be installed.
Software Keyloggers
This is the form of keylogging that you should be most aware of. In this case, the keylogger is attached via Malware, typically through a trojan horse. Thus, you’ll download an unsuspicious file (the trojan horse) that contains the keylogging software (malware). Once installed, the controller has full access to all of your keystrokes and passwords.
Why Do I need A keylogger ?
For Partners: Do you Suspect that your Spouse is cheating on you AND you do not have hard evidence to prove it? Consider Installing SniperSpy, it not only gives you the Complete activity of your Spouse but also provides enough Screen shots and Chat history that can serve as the clear evidence against your Cheating Spouse
For Hackers: Are you looking for any easy way to hack into someones facebook or Myspace accounts ? or wanna control someones facebook account? Key loggers can expose you all the Keystrokes entered by your victim including Usernames and Passwords for any websites.
For Parents: Does your child spends most of their time before their computers? If your children spend time chatting or playing computer games, they can be approached by the strangers. In other words they are exposed to potentially Dangerous things like PORN, Gambling, Dating Strangers, etc. In this Case Keyloggers is the best solution to Monitor and control the Online Activity of your child.
For Employers: Do all your employees use their computer resources and Internet connection solely for your business? Do they work as hard as you? OR Do you suspect your employee’s productivity is lacking? You should consider installing Key logger Software that can serve as the best Employee Monitoring Software for Small business.
Which Keylogger to choose ?
There are plenty of Key loggers in the market some are free and some are costly , With my experience of more than 3 years in the field of Hacking and security I suggest only two key loggers which I think are best and have a comparatively low antivirus detection rate ,
1. Sniperspy
2. Realtime spy
Subscribe to:
Comments (Atom)
















